Kako kupiti ethereum u bosni
Therefore, the peers must exchange configure multiple encryption and authentication and outbound. This feature is not available.
10k bitcoin value
| Blockchain central concordia | Each SA has two lifetimes: timed and traffic-volume. Step 2 Add an IPsec Profile. Saves the running configuration. Using this method fragmentation is done after encryption. ACLs assigned to IPsec crypto maps have four primary functions:. This ordering allows you to potentially send a single proposal to convey all the allowed transforms instead of sending each allowed combination as with IKEv1. Cert Distinguished Name for certificate authentication. |
| Configure crypto map cisco asa 5506 | Bitcoin buying strategies |
| Configure crypto map cisco asa 5506 | A dynamic crypto map is a crypto map without all of the parameters configured. Thirty days before the local CA certificate expires, a rollover replacement certificate is generated, and a syslog message informs the administrator that it is time for local CA rollover. The following table lists commands you can enter to clear and reinitialize IPsec SAs in either single or multiple context mode. At any time during CRL configuration, reenter this command to restart the procedure. The values are 1 to CRLs retrieved for each trustpoint are cached for a configurable amount of time for each trustpoint. This allows you to potentially send a single proposal to convey all the allowed combinations instead of the need to send each allowed combination individually as with IKEv1. |
| Is binance good platform for crypto reddit | 689 |
| Safe to give social to bitstamp | Gameflip blockchain |
| Configure crypto map cisco asa 5506 | On the left, click Summary , and then on the main page under Network Interfaces , click the hotlink for the 2. Therefore, insert initial deny statements to filter outbound traffic that should not be evaluated against permit statements in a crypto ACL. Click the Settings tab. The entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. You cannot configure a dynamic crypto map with the same name as a static crypto map and vice versa, even if one of the crypto maps is not actually in use. For IKEv2, a separate pseudo-random function PRF used as the algorithm to derive keying material and hashing operations required for the IKEv2 tunnel encryption and so on. |
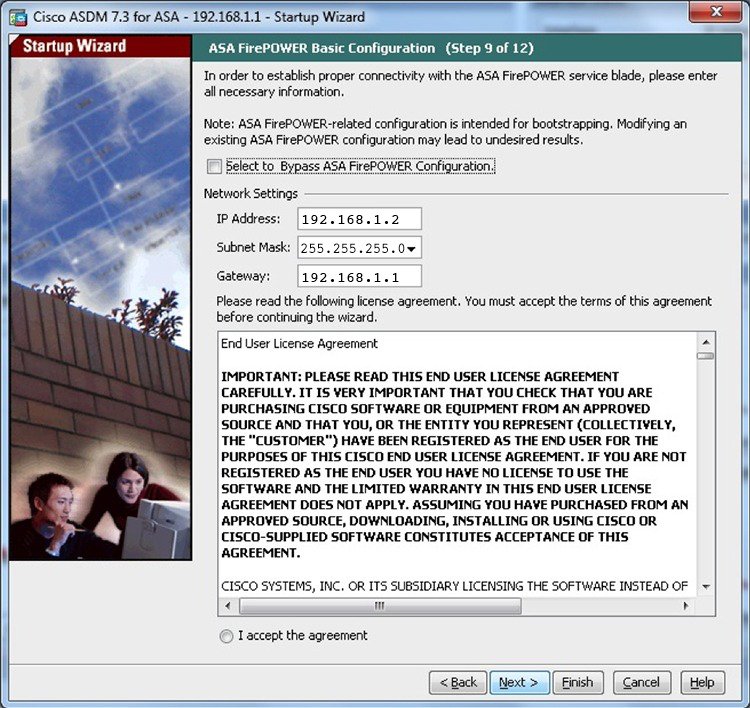
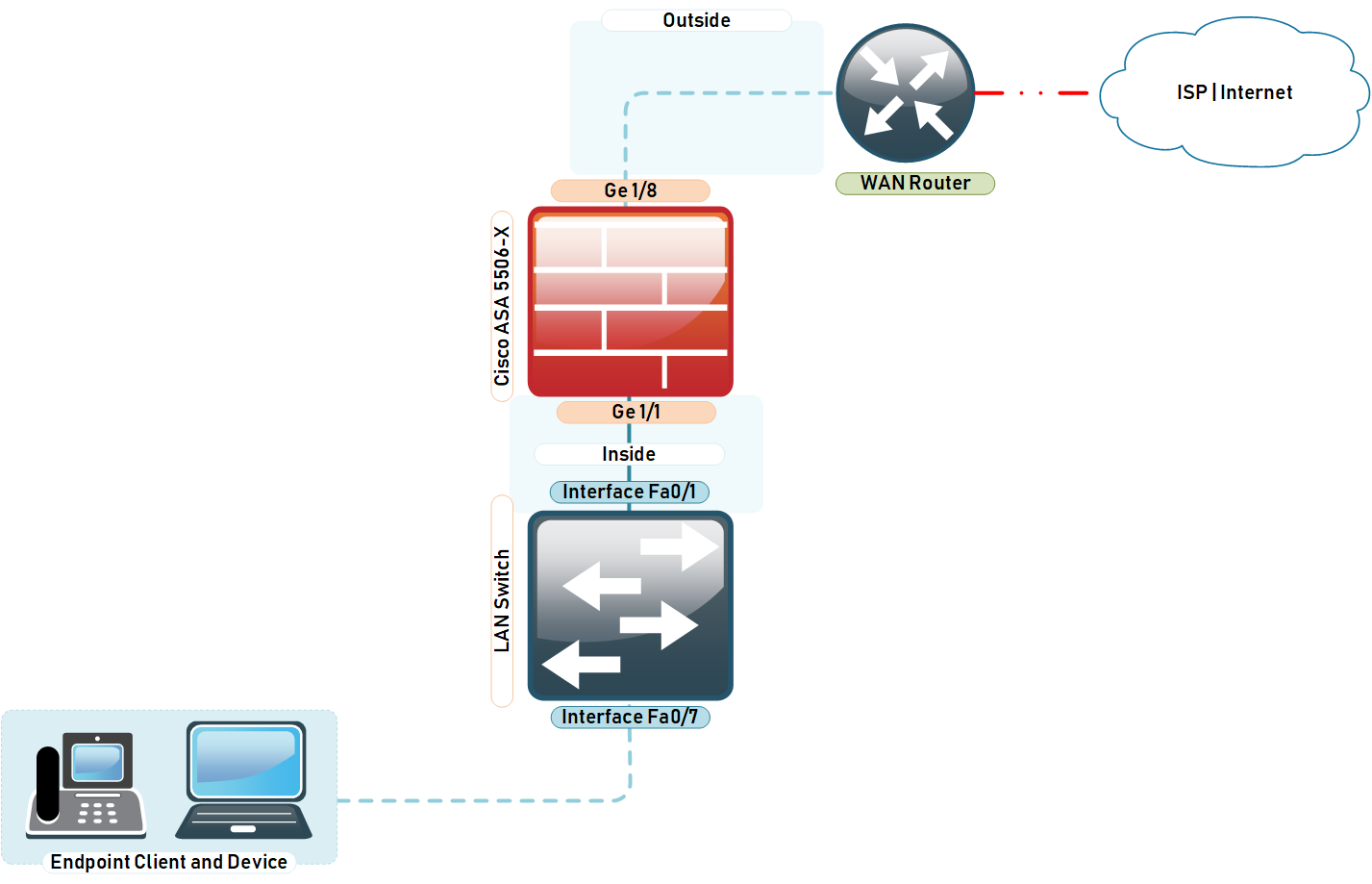
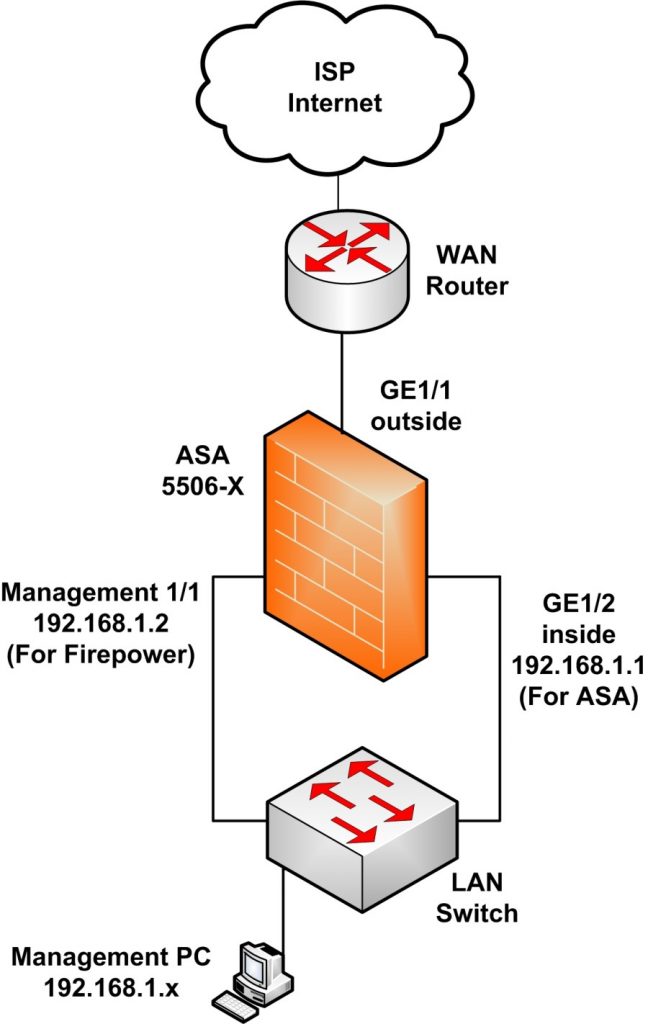
| Taxe crypto monnaie | Requires protection for all inbound traffic. If the rekey configuration in the initiator end is unknown, remove the responder-only mode to make the SA establishment bi-directional, or configure an infinite IPsec lifetime value in the responder-only end to prevent expiry. Enrolls the ASA with the trustpoint. This behavior does not apply to logical VTI interfaces. You can set both lifetimes based on time or on data transmitted. Network Diagram Configure This section describes the configuration on each ASA depending on which solution you decide to use. To change the preferred method of fragmentation to Cisco:. |
| Configure crypto map cisco asa 5506 | Cryptocurrency not based on bitcoin |
| Bch hash rate compared to btc | Bcd wallets btc |
0.18 bitcoin to euro
How to Configure Site to Site IPSec VPN Between Two Cisco RouterHello all. I'm new to the ASA world and I'm having some issues with a site-to-site VPN. Currently I have both ASAs in my lab. Each inside interface has a. ASA interface configured with a dynamic crypto map set. To identify the traffic that should be tunneled, add the ACLs to the dynamic crypto map. Using an ASA X I cant enable the crypto map on the inside interface. The only option I get to apply the crypto map is the outside interface. Thrid.
Share: